Ngnix


Please feel free to contact us
Go
Nginx (pronounced “engine-x”) is a high-performance web server and reverse proxy server known for its speed, scalability, and ability to handle many simultaneous connections. Nginx is a versatile tool suitable for a variety of web serving tasks. Whether hosting a simple website or managing a complex application infrastructure, Nginx’s performance and features make it a popular choice among developers and system administrators. Here’s a comprehensive overview:
You can subscribe to Nginx 1.24, an AWS Marketplace product and launch an instance from the product’s AMI using the Amazon EC2 launch wizard.
Step 1: SSH into Your Instance: Use the SSH command with the username ubuntu and the appropriate key pair to access your instance.
Username: ubuntu
ssh -i path/to/ssh_key.pem ubuntu@instance-IP
Replace path/to/ssh_key.pem with the path to your SSH key file and instance-IP with the public IP address of your instance.
Step 2: At the terminal, write a command to check that the Nginx is successfully installed.
systemctl status nginx
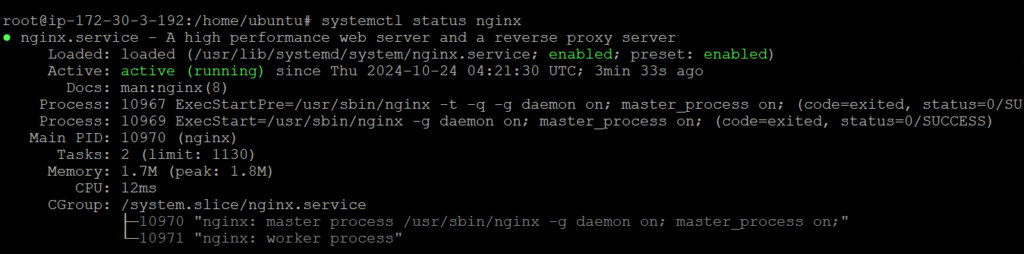
You can also check by navigating to http://instance-ip.
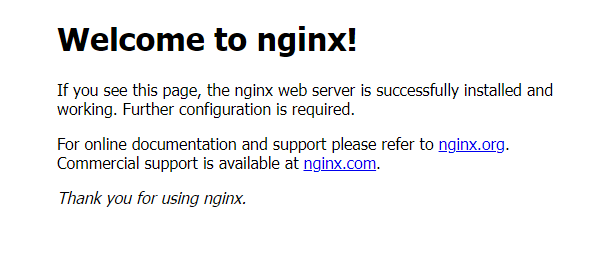
Step 3: Managing Nginx
sudo systemctl start nginxsudo systemctl stop nginxsudo systemctl restart nginxsudo systemctl status nginxsudo nginx -tAll your queries are important to us. Please feel free to connect.
24X7 support provided for all the customers.
We are happy to help you.
Submit your Query: https://miritech.com/contact-us/
Contact Numbers:
Contact E-mail:
Amazon EC2 allows you to set up and configure everything about your instances from your operating system up to your applications. An Amazon Machine Image (AMI) is simply a packaged-up environment that includes all the necessary bits to set up and boot your instance. Your AMIs are your unit of deployment. You might have just one AMI or you might compose your system out of several building block AMIs (e.g., webservers, appservers, and databases). Amazon EC2 provides a number of tools to make creating an AMI easy. Once you create a custom AMI, you will need to bundle it. If you are bundling an image with a root device backed by Amazon EBS, you can simply use the bundle command in the AWS Management Console. If you are bundling an image with a boot partition on the instance store, then you will need to use the AMI Tools to upload it to Amazon S3. Amazon EC2 uses Amazon EBS and Amazon S3 to provide reliable, scalable storage of your AMIs so that we can boot them when you ask us to do so.
Or, if you want, you don’t have to set up your own AMI from scratch. You can choose from a number of globally available AMIs that provide useful instances. For example, if you just want a simple Linux server, you can choose one of the standard Linux distribution AMIs.
No. You do not need an Elastic IP address for all your instances. By default, every instance comes with a private IP address and an internet routable public IP address. The private address is associated exclusively with the instance and is only returned to Amazon EC2 when the instance is stopped or terminated. The public address is associated exclusively with the instance until it is stopped, terminated or replaced with an Elastic IP address. These IP addresses should be adequate for many applications where you do not need a long lived internet routable end point. Compute clusters, web crawling, and backend services are all examples of applications that typically do not require Elastic IP addresses.
Amazon EC2 security groups can be used to help secure instances within an Amazon VPC. Security groups in a VPC enable you to specify both inbound and outbound network traffic that is allowed to or from each Amazon EC2 instance. Traffic which is not explicitly allowed to or from an instance is automatically denied.
In addition to security groups, network traffic entering and exiting each subnet can be allowed or denied via network Access Control Lists (ACLs).
Amazon S3 is secure by default. Upon creation, only the resource owners have access to Amazon S3 resources they create. Amazon S3 supports user authentication to control access to data. You can use access control mechanisms such as bucket policies and Access Control Lists (ACLs) to selectively grant permissions to users and groups of users. The Amazon S3 console highlights your publicly accessible buckets, indicates the source of public accessibility, and also warns you if changes to your bucket policies or bucket ACLs would make your bucket publicly accessible.
You can securely upload/download your data to Amazon S3 via SSL endpoints using the HTTPS protocol. If you need extra security you can use the Server-Side Encryption (SSE) option to encrypt data stored at rest. You can configure your Amazon S3 buckets to automatically encrypt objects before storing them if the incoming storage requests do not have any encryption information. Alternatively, you can use your own encryption libraries to encrypt data before storing it in Amazon S3.
Amazon RDS manages the work involved in setting up a relational database: from provisioning the infrastructure capacity you request to installing the database software. Once your database is up and running, Amazon RDS automates common administrative tasks such as performing backups and patching the software that powers your database. With optional Multi-AZ deployments, Amazon RDS also manages synchronous data replication across Availability Zones with automatic failover.
Since Amazon RDS provides native database access, you interact with the relational database software as you normally would. This means you’re still responsible for managing the database settings that are specific to your application. You’ll need to build the relational schema that best fits your use case and are responsible for any performance tuning to optimize your database for your application’s workflow.
Reverse Proxy: Can serve as a reverse proxy, handling requests from clients and forwarding them to backend servers.
Load Balancing: Distributes incoming traffic across multiple servers to ensure high availability and reliability.
Static Content: Efficiently serves static files (HTML, CSS, images) with low latency.
SSL/TLS Support: Offers built-in support for secure connections, including SSL and TLS.
URL Rewriting: Allows for flexible URL management and redirection.
Concurrent Connections: Can handle a large number of simultaneous connections, making it ideal for high-traffic websites.
 Nginx 1.24
Nginx 1.24