Memcached


Please feel free to contact us
Go
A high-performance, distributed memory object caching system, generic in nature called Memcached is intended for use in speeding up dynamic web applications by alleviating database load.
Memcached is an in-memory key-value store for small chunks of arbitrary data (strings, objects) from results of database calls, API calls, or page rendering. The simplicity of its design promotes quick deployment, ease of development, and solves many problems facing large data caches. Its API is available for most popular languages.
Miri Infotech is launching a product which will configure and publish Memcache, to produce free implementations of distributed or otherwise scalable and high availability which is embedded pre-configured tool and ready-to-launch AMI on Amazon EC2 that contains MariaDB.
Memcached basically runs on Unix-like operating systems and on Microsoft Windows. It depends on the libevent library.
A large hash table is provided by its APIs. Applications using Memcached typically layer requests and additions into RAM before falling back on a slower backing store, such as a database.
This is the general knowledge that one must have before started working on Memcache.
Let us now know what exactly its software architecture is and what its functionalities are.
The system uses a client-server architecture. The servers maintain a key–value associative-array; the clients populate this array and query it by key. The length of the Keys are up to 250 bytes and values can be at most 1 megabyte in size.
If we talk about the typical deployment of this architecture then it can have several servers and many clients. However, it is possible to use Memcached on a single computer, acting simultaneously as client and server. The size of its hash table is often very large. It is limited to available memory across all the servers in the cluster of servers in a data center. Where high-volume, wide-audience Web publishing requires it, this may stretch too many gigabytes.
Now talking about MariaDB, we can say that it is one of the most popular database server which is being widely used.
MariaDB turns data into structured information in a wide array of applications, ranging from banking to websites. It is an enhanced, drop-in replacement for MySQL. It is used because it is fast, scalable and robust, with a rich ecosystem of storage engines, plugins and many other tools make it very versatile for a wide variety of use cases.
MariaDB intends to maintain high compatibility with MySQL, ensuring a drop-in replacement capability with library binary equivalency and exact matching with MySQL APIs and commands.
Not only this but MariaDB provides much more than MySQL be it related to security, support etc. MariaDB development is more open and vibrant.
MariaDB combined with Memcached and Lamp provides a better and fast cached server with high level of flexibility and ease of use.
You can subscribe Memcached to an AWS Marketplace product and launch an instance from the Memcached product’s AMI using the Amazon EC2 launch wizard.
Step 1: SSH into Your Instance: Use the SSH command with the username ubuntu and the appropriate key pair to start the application.
Username: ubuntu
ssh -i path/to/ssh_key.pem ubuntu@instance-IP
Replace path/to/ssh_key.pem with the path to your SSH key file and instance-IP with your instance’s public IP address.
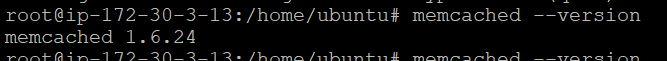
Step 2: Now, you can enter the following command to check the applications installed successfully.
memcached --version
Step 3: You can enter the following command to run the application.
php memcached.php
![]()
All your queries are important to us. Please feel free to connect.
24X7 support provided for all the customers.
We are happy to help you.
Submit your Query: https://miritech.com/contact-us/
Contact Numbers:
Contact E-mail:
Instances without public IP addresses can access the Internet in one of two ways:
No. You do not need an Elastic IP address for all your instances. By default, every instance comes with a private IP address and an internet routable public IP address. The private address is associated exclusively with the instance and is only returned to Amazon EC2 when the instance is stopped or terminated. The public address is associated exclusively with the instance until it is stopped, terminated or replaced with an Elastic IP address. These IP addresses should be adequate for many applications where you do not need a long lived internet routable end point. Compute clusters, web crawling, and backend services are all examples of applications that typically do not require Elastic IP addresses.
You have complete control over the visibility of your systems. The Amazon EC2 security systems allow you to place your running instances into arbitrary groups of your choice. Using the web services interface, you can then specify which groups may communicate with which other groups, and also which IP subnets on the Internet may talk to which groups. This allows you to control access to your instances in our highly dynamic environment. Of course, you should also secure your instance as you would any other server.
Amazon S3 provides a simple web service interface that you can use to store and retrieve any amount of data, at any time, from anywhere on the web. Using this web service, you can easily build applications that make use of Internet storage. Since Amazon S3 is highly scalable and you only pay for what you use, you can start small and grow your application as you wish, with no compromise on performance or reliability.
Amazon S3 is also designed to be highly flexible. Store any type and amount of data that you want; read the same piece of data a million times or only for emergency disaster recovery; build a simple FTP application, or a sophisticated web application such as the Amazon.com retail web site. Amazon S3 frees developers to focus on innovation instead of figuring out how to store their data
By default, Amazon RDS chooses the optimal configuration parameters for your DB Instance taking into account the instance class and storage capacity. However, if you want to change them, you can do so using the AWS Management Console, the Amazon RDS APIs, or the AWS Command Line Interface. Please note that changing configuration parameters from recommended values can have unintended effects, ranging from degraded performance to system crashes, and should only be attempted by advanced users who wish to assume these risks.
Amazon S3 is secure by default. Upon creation, only the resource owners have access to Amazon S3 resources they create. Amazon S3 supports user authentication to control access to data. You can use access control mechanisms such as bucket policies and Access Control Lists (ACLs) to selectively grant permissions to users and groups of users. The Amazon S3 console highlights your publicly accessible buckets, indicates the source of public accessibility, and also warns you if changes to your bucket policies or bucket ACLs would make your bucket publicly accessible.
You can securely upload/download your data to Amazon S3 via SSL endpoints using the HTTPS protocol. If you need extra security you can use the Server-Side Encryption (SSE) option to encrypt data stored at rest. You can configure your Amazon S3 buckets to automatically encrypt objects before storing them if the incoming storage requests do not have any encryption information. Alternatively, you can use your own encryption libraries to encrypt data before storing it in Amazon S3.
When a minor version of a database engine is deprecated in Amazon RDS, we will provide a three (3) month period after the announcement before beginning automatic upgrades. At the end of the this period, all instances still running the deprecated minor version will be scheduled for automatic upgrade to the latest supported minor version during their scheduled maintenance windows.
When a major version of database engine is deprecated in Amazon RDS, we will provide a minimum six (6) month period after the announcement of a deprecation for you to initiate an upgrade to a supported major version. At the end of this period, an automatic upgrade to the next major version will be applied to any instances still running the deprecated version during their scheduled maintenance windows.
Once a major or minor database engine version is no longer supported in Amazon RDS, any DB instance restored from a DB snapshot created with the unsupported version will automatically and immediately be upgraded to a currently supported version.
A Rich Ecosystem of Storage Engines and plugins
Key-Value store for small chunks of arbitrary data
A large hash table is provided in it
 Memcached
Memcached  php
php  linux
linux